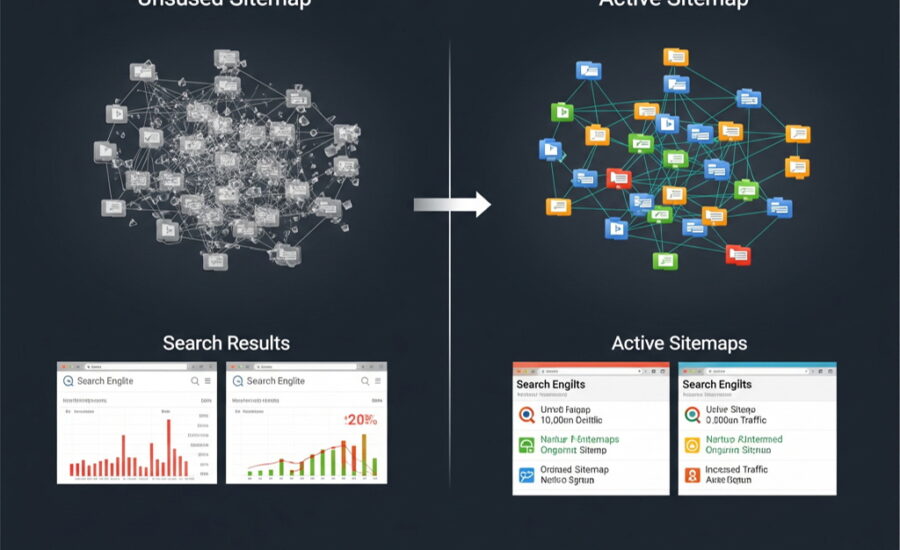
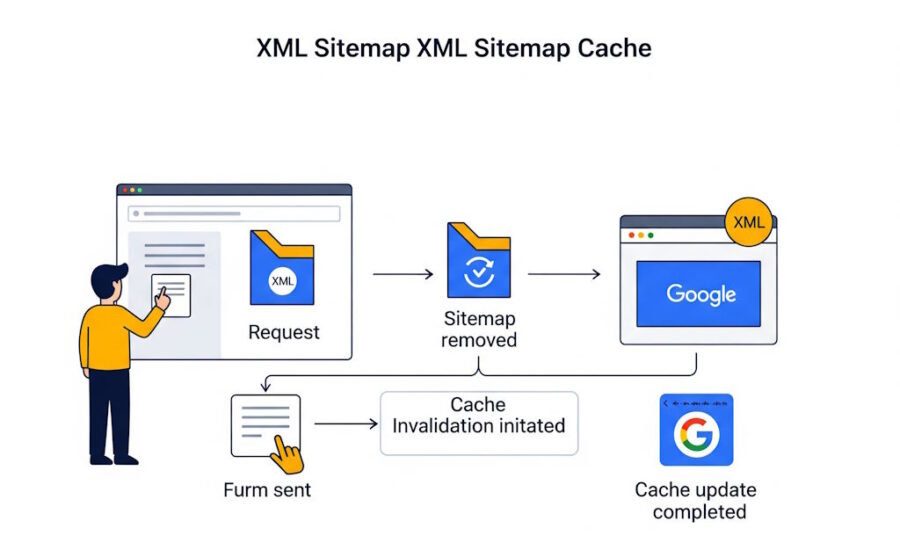
If a sitemap.xml is no longer in use, there are a few options to handle it, each with different implications. Here’s what you should consider: Options for Handling an Unused Sitemap Completely Delete the Sitemap: Advantages: Ensures
Blog Standard
- Home
- Blog Standard
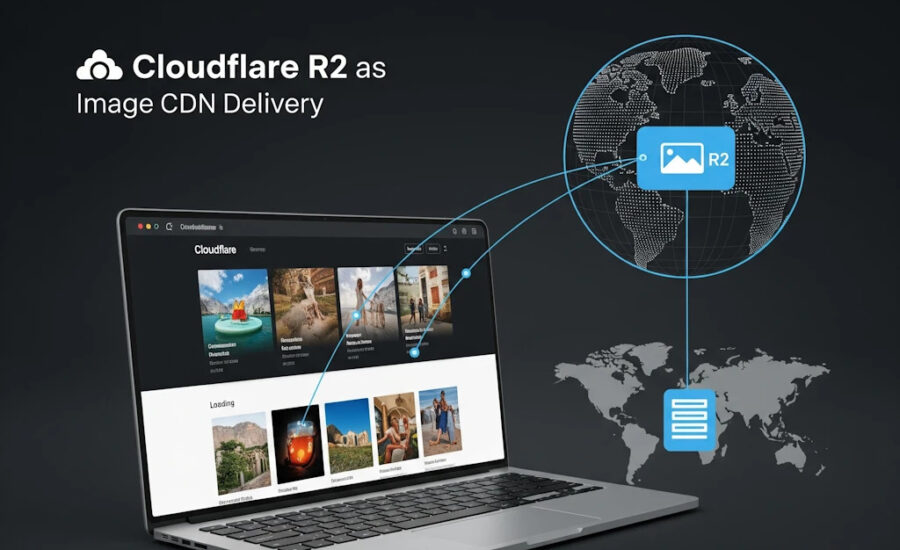
Implementing Cloudflare R2 as an Image CDN on your website involves a few steps, from setting up the R2 bucket to configuring your website to serve images from R2. Here's a step-by-step guide to get you started:
You can use Cloudflare R2 as an image CDN. Cloudflare R2 is a highly scalable object storage service that is designed to store large amounts of unstructured data, including images, videos, and other types of files. Here
A "DNS Server Spoofed Request Amplification DDoS" vulnerability indicates that your DNS server can be exploited to participate in Distributed Denial of Service (DDoS) attacks. Attackers can send DNS queries with a spoofed source IP address (the
Conducting a comprehensive keyword analysis for your website and the main competitors is a strategic approach to enhance your SEO performance. Here's a step-by-step guide to help you identify popular keywords and optimize your website accordingly: 🔍
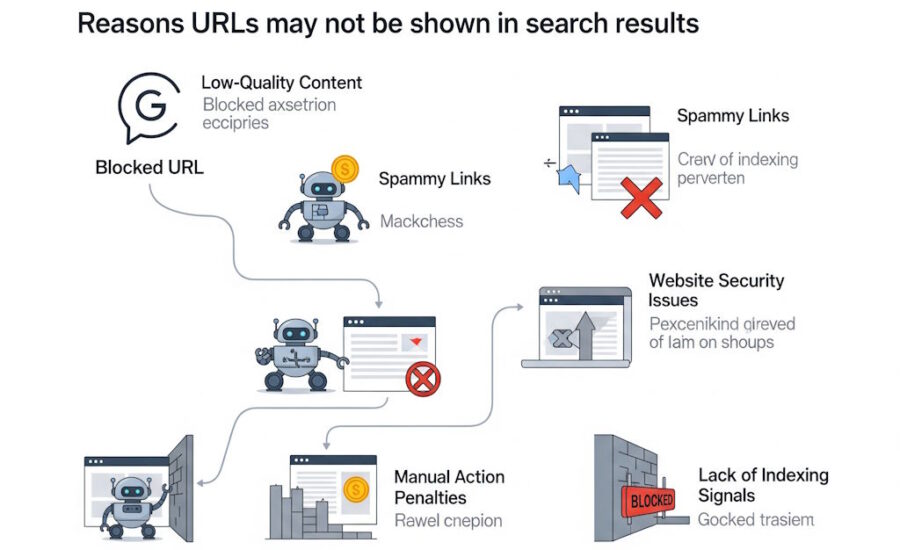
The unavailable_after meta tag is used to inform search engines like Google that a specific page should be removed from the search engine results after a certain date. This can be particularly useful for content with a
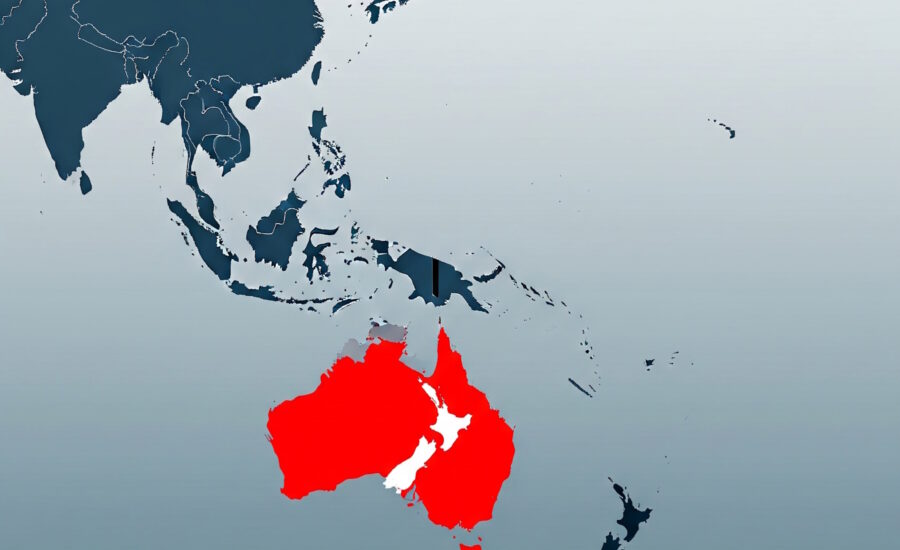
There is this global domain name for the website abcde.com, but the site is only commercially available in Australia and New Zealand. The site also has 2 URLs for 2 countries. abcde.com/nz and abcde.com/au. The question is,
SEO Case Study There's an online advertising business at www.taka8.com, there's a URL for a city at www.taka8.com/auckland, and there's a lot of adverts listed underneath that city at www.taka8.com/auckland/ad1, www.taka8.com/auckland/ad2, www. taka8.com/auckland/ad3, etc. All these URLs
In New Zealand, several ethical frameworks and guidelines are used to guide ethical analysis in data governance, particularly in the context of research and data handling. These frameworks are designed to ensure that data management practices adhere
If an old XML sitemap is deleted, Google may remember it for a while but will eventually stop attempting to crawl it if it is no longer accessible. However, it’s best to take proactive steps to inform
- 1
- 2